Microsoft identified the vulnerability of the Web Proxy Auto-Discovery (WPAD) protocol in 2007, which could potentially be exploited to access secure HTTPS and VPN data. However, developers did not take significant measures to address this issue, possibly because the WPAD vulnerability was not considered a direct threat, but rather a potential and relatively uncommon one.
What is WPAD
The Web Proxy Auto-Discovery Protocol (WPAD) is a collection of rules for automatic proxy configuration. It is employed by web browsers to locate the URL of the PAC configuration file, which then calls the FindProxyForURL function to provide a list of proxies to the client.
However, the WPAD vulnerability can enable the interception and redirection of browser requests through controlled proxy servers to fake PAC files or sites. This interception is only possible in an open Wi-Fi network, and therefore, disabling WPAD is particularly relevant when using public networks.
You can use the the Registry Editor to disable the affected protocol. Do the following.
How to disable WPAD
- Run regedit.
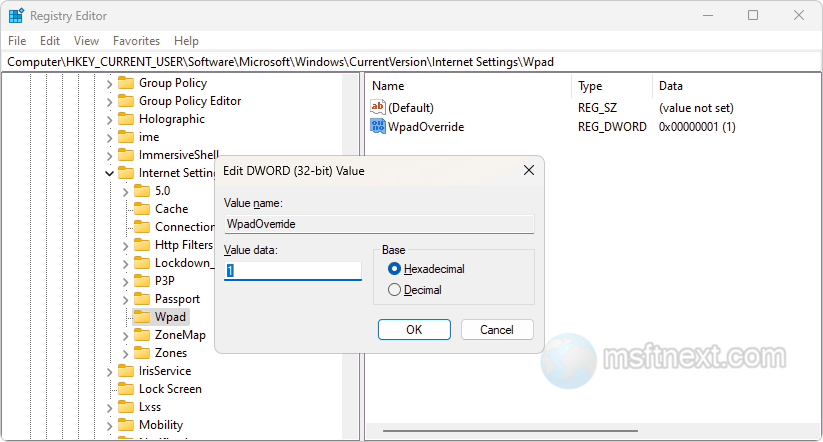
- Navigate to this branch: HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad.
- Create a DWORD value in the last subkey, Wpad. Name it WpadOverride and set its value to
1.
Disabe WPAD - Now, disable DNS Multicast by opening the HKLM\Software\policies\Microsoft\Windows NT\DNSClient key.
- Create a DWORD value “EnableMulticast” in the DNSClient key and keep its value zeroed.
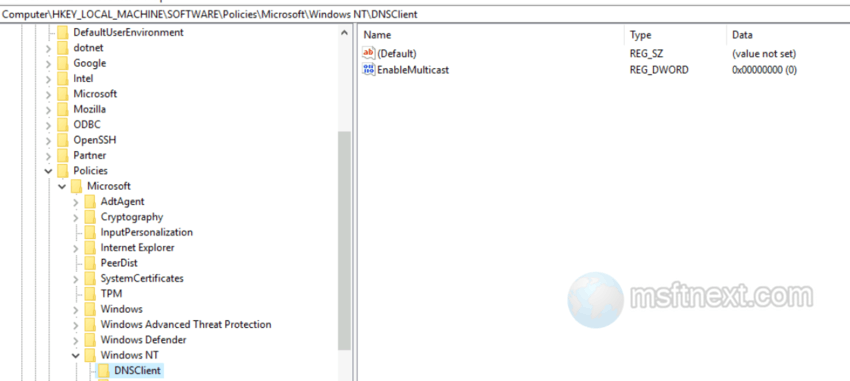
disable DNS Multicast - You can also disable the Web Proxy Auto-Detection service. Navigate to HKLM\SYSTEM\CurrentControlSet\Services\WinHttpAutoProxySvc.
- Find the Start parameter on the right and change its value to
4. - Restart your computer.
This should keep your device protected.
Command prompt method
You can disable WPAD and LLMNR on Windows with the commands below. Run these commands on Windows as an administrator to stop WPAD and LLMNR attacks (e.g. the Responder attack).
REG ADD "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad"REG ADD "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad" /v "WpadOverride" /t REG_DWORD /d "1" /f
REG ADD "HKLM\Software\policies\Microsoft\Windows NT\DNSClient"REG ADD "HKLM\Software\policies\Microsoft\Windows NT\DNSClient" /v "EnableMulticast" /t REG_DWORD /d "0" /f
sc config stop WinHttpAutoProxySvcsc config disable WinHttpAutoProxySvc
The Local Group Policy method
- Open Group Policy Editor(gpedit.msc).
- Go to User Configuration \ Policies \Windows Settings \Connection\Automatic Browser Configuration.
- Set Automatically detect configuration settings to DISABLE.
While disabling WPAD can lower the risk of encountering issues when connecting to public wireless networks, it is still recommended to avoid using such networks unless it is essential.
